access control based on smart card strategies Thales' smart cards offer a single solution for strong authentication and applications access control, including remote access, network access, password management, network logon, as well as corporate ID badges, magnetic stripes and proximity.
While you can get unlimited amounts of Champion's Tunics or Hylian Shields, there can only be one Master Sword. The chests summoned by Legend of Zelda amiibo are styled after the chests from The Legend of Zelda: Breath of the Wild and play the "discovered-a-secret" chime from .There are 3 requirements for making amiibos you can use on your Switch/Wii U/3DS. NFC writing capability - generally this means only Android phones with NFC, but apparently it is possible to buy an NFC reader/writer for PC but it is .
0 · types of access control cards
1 · smart card door access system
2 · smart card access control systems
3 · identisys swipe access card
4 · hid card access control system
5 · hid access control system installation
6 · hid access card log in
7 · employee door access control
64. This project showcases how to exploit vulnerabilities in NFC cards using Arduino and RFID technology. By leveraging the MFRC522 RFID module, you can read and write data on NFC cards. The code provided offers a foundation .The latest update is all about RFID and NFC, and how the Flipper Zero can interact with a variety of contactless protocols. Contactless tags are broadly separated into low-frequency (125 kHz) and .
Smart cards can process data, carry out commands, and secure information thanks to recent advancements in circuit chip technology. In this comprehensive guide, we’ll dive into different types of smart cards for access control, their functionalities, and their uses in .As an access-control device, smart cards (company badges, university IDs) make personal and business data available only to the appropriate users. As a National eID card , smart health card , residence permit, or electronic passport , smart card technology offers more robust identification and authentication tools for both authorities' and . Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to resources. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access.
In fact, conducting an annual access control system review is the first step in establishing a systematic process for assessing the security of your organization; it is the principle best practice that provides the framework for all the other guidelines.
Strategies for high-security authentication. Jennifer Toscano. A smart card reader can attached to or embedded into a biometric reader. When creating an access control system, it is important.Thales' smart cards offer a single solution for strong authentication and applications access control, including remote access, network access, password management, network logon, as well as corporate ID badges, magnetic stripes and proximity.Centralization and distribution access control models are most appropriate for smart cards. Smart cards can be used for PC access control, provided that changes to smart card infrastructure are completed.
The Smart ID cards control physical access to secure facilities and logical access to IT Systems ( servers, Database Servers, Workstations) and applications. The authentication of the card and the holder takes place using a set of credentials.For decades, HID has helped millions of people easily access offices, hospitals, classrooms and more. From entry-level smart card technologies to modern solutions like HID Mobile Access, our mission is to help your organization find the best access control solution.Smart cards in access control. A smart card is a typical plastic card that contains an embedded computer chip which is either a memory or a microprocessor type. The data the chip responsible for storing and transmitting is connected to value, information, or a combination of both. This data is both stored and processed within the card’s chip. Smart cards can process data, carry out commands, and secure information thanks to recent advancements in circuit chip technology. In this comprehensive guide, we’ll dive into different types of smart cards for access control, their functionalities, and their uses in .
As an access-control device, smart cards (company badges, university IDs) make personal and business data available only to the appropriate users. As a National eID card , smart health card , residence permit, or electronic passport , smart card technology offers more robust identification and authentication tools for both authorities' and .
types of access control cards
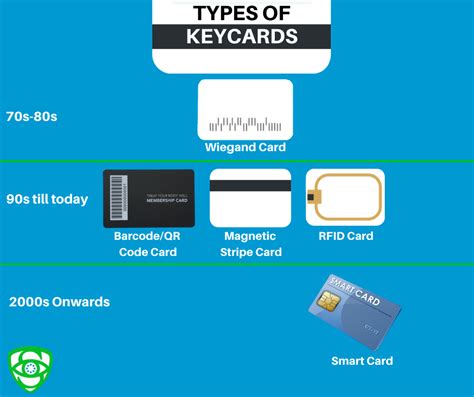
Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to resources. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access.In fact, conducting an annual access control system review is the first step in establishing a systematic process for assessing the security of your organization; it is the principle best practice that provides the framework for all the other guidelines.
cryptocurrency mastercard contactless card hungary
Strategies for high-security authentication. Jennifer Toscano. A smart card reader can attached to or embedded into a biometric reader. When creating an access control system, it is important.Thales' smart cards offer a single solution for strong authentication and applications access control, including remote access, network access, password management, network logon, as well as corporate ID badges, magnetic stripes and proximity.Centralization and distribution access control models are most appropriate for smart cards. Smart cards can be used for PC access control, provided that changes to smart card infrastructure are completed.
The Smart ID cards control physical access to secure facilities and logical access to IT Systems ( servers, Database Servers, Workstations) and applications. The authentication of the card and the holder takes place using a set of credentials.For decades, HID has helped millions of people easily access offices, hospitals, classrooms and more. From entry-level smart card technologies to modern solutions like HID Mobile Access, our mission is to help your organization find the best access control solution.
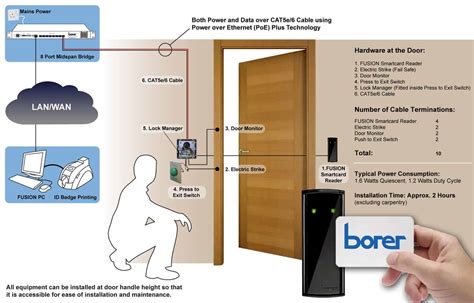
smart card door access system
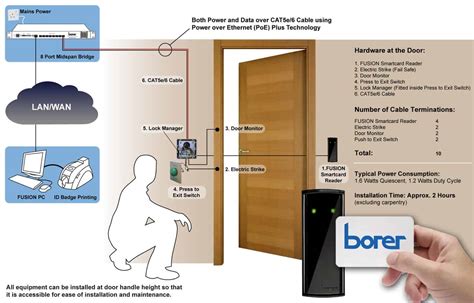
smart card access control systems

contactless visa card india
crypto visa contactless card slovenia
In this Cemu 1.9.0 guide i show you how to use Amiibos via NFC tag scanning with The Legend of Zelda Breath of the Wild.Previous BOTW Editor Video (Partially.
access control based on smart card strategies|hid card access control system