decrypt rfid tag RFID tags can be cloned. Tags which do not make use of password-protection or . If I were to build the code myself, do iPhones or popular Android phones .
0 · rfid tags decoder
1 · rfid tag type
2 · rfid subfamily
3 · pepperl rfid tag type
4 · how to read rfid tags
5 · bambulab rfid tags
6 · bambulab mifare rfid
The TappyUSB is an enterprise-grade, all-in-one NFC encoder that is easily integrated into your NFC solutions and applications. Read and write to the most popular NFC chips (ISO 14443 A/B, Tag Types 1,2,3, and 4.) Focus on writing .
RFID tags can be cloned. Tags which do not make use of password-protection or .If you have a Proxmark3 (or other RFID debugging tool), you can sniff and decrypt the contents of your tags and submit them for review. The more data we have, the easier it is to compare differences to learn what each byte represents. RFID tags can be cloned. Tags which do not make use of password-protection or over-the-air (OTA) encryption can have their data banks copied into new tags. RFID tags (at least Class 1 Generation 2 tags, aka UHF RFID tags) are computationally active, not passive.
Pepperl+Fuchs’ RFID read/write heads can read any RFID tags made to this standard and, at the same time, any RFID system can read Pepperl+Fuchs’ RFID tags. In this blog article, we explain how to decode HF RFID tags to configure your HF RFID system.
Radio Frequency Identification (RFID), is a technology that uses electromagnetic fields to automatically identify and/or track “tags” that contain electronically stored information. Some tags are passive, therefore they are activated by the electromagnetic fields generated by nearby readers.The Darkside attack leverages the RFID tag’s response to an RFID reader’s request signal during key authentication. Along with every nonce sent from the reader to the tag is an accompanying 8 parity bits that must match up with the tag in order for it to send a response signal. I need to write strings to an RFID Tag (which is already what I'm doing). But now before writing the message I want to Encrypt it then write it. After reading I decrypt the message and receive the actual string. Doing so, I will be the only person capable of .
All radio frequency data transmission between the tag and reader is encrypted using a secure algorithm. By using industry standard encryption techniques, iCLASS reduces the risk of compromised data or duplicated tags. For even higher security, the tag data may also be protected with DES or triple-DES encryption. In this blog article, we explain how to decode HF RFID tags to configure your HF RFID system. What Is a Tag Type? The openness of the RFID system has allowed several manufacturers to produce chips, i.e. electronics that are included in the RFID tag, making the overall tag price very competitive.RFIDcoder is a REST API for encoding and decoding UHF Gen2 RFID tags according to the GS1 EPC Tag Data Standard.You can decrypt millions of RFID tag encryptions and NFC encryptions without filling up storage space on a smart phone or OEM scanning device. Additionally, since Microtrace’s encrypted data string can be authenticated on your local device, the result is instantaneous, compared to traditional encryption methodologies, which require several .
If you have a Proxmark3 (or other RFID debugging tool), you can sniff and decrypt the contents of your tags and submit them for review. The more data we have, the easier it is to compare differences to learn what each byte represents.
rfid tags decoder
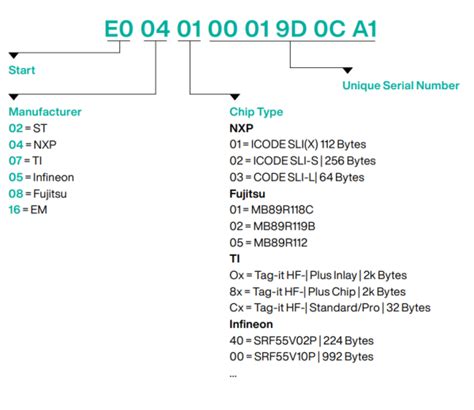
RFID tags can be cloned. Tags which do not make use of password-protection or over-the-air (OTA) encryption can have their data banks copied into new tags. RFID tags (at least Class 1 Generation 2 tags, aka UHF RFID tags) are computationally active, not passive. Pepperl+Fuchs’ RFID read/write heads can read any RFID tags made to this standard and, at the same time, any RFID system can read Pepperl+Fuchs’ RFID tags. In this blog article, we explain how to decode HF RFID tags to configure your HF RFID system.
auburn california radio stations
Radio Frequency Identification (RFID), is a technology that uses electromagnetic fields to automatically identify and/or track “tags” that contain electronically stored information. Some tags are passive, therefore they are activated by the electromagnetic fields generated by nearby readers.The Darkside attack leverages the RFID tag’s response to an RFID reader’s request signal during key authentication. Along with every nonce sent from the reader to the tag is an accompanying 8 parity bits that must match up with the tag in order for it to send a response signal. I need to write strings to an RFID Tag (which is already what I'm doing). But now before writing the message I want to Encrypt it then write it. After reading I decrypt the message and receive the actual string. Doing so, I will be the only person capable of .
All radio frequency data transmission between the tag and reader is encrypted using a secure algorithm. By using industry standard encryption techniques, iCLASS reduces the risk of compromised data or duplicated tags. For even higher security, the tag data may also be protected with DES or triple-DES encryption. In this blog article, we explain how to decode HF RFID tags to configure your HF RFID system. What Is a Tag Type? The openness of the RFID system has allowed several manufacturers to produce chips, i.e. electronics that are included in the RFID tag, making the overall tag price very competitive.RFIDcoder is a REST API for encoding and decoding UHF Gen2 RFID tags according to the GS1 EPC Tag Data Standard.
rfid tag type

rfid subfamily

auburn kentucky radio broadcast
auburn kentucky basketball radio
The problems seems to be that it's not possible to emulate/modify the sector 0, .
decrypt rfid tag|bambulab mifare rfid