rfid chips secuirty A small chip -- known as an RFID tag -- is attached to or implanted in an object. The tags contain information that can be read at short range via radio waves. The chip and . I have a NXP MIFARE DESFire Ev2 that also just in some rare cases get's read successfully by the Flipper Zero as ISO 14443-4A (Unknown) but in 90% of the time it just hangs in Reading card, Don't move.. The card is a .The FloBLE Module is an NFC Reader that connects to mobile devices via USB. It supports all the ISO14443 protocols for interacting with passive tags as well as mobile wallets (e.g. VAS, ECP, SmartTap). The mini does not include a battery and is designed to draw .
0 · where are rfid chips used
1 · types of rfid chips
2 · rfid chips in humans
3 · rfid chips for sale
4 · rfid chip pros and cons
5 · rfid chip meaning
6 · rfid chip manufacturing
7 · pros and cons of rfid
Check the Browser compatibility table carefully before using this in production. The NDEFReader interface of the NFC API is used to read from and write data to compatible .
A small chip -- known as an RFID tag -- is attached to or implanted in an object. The tags contain information that can be read at short range via radio waves. The chip and . RFID chips are a convenient way to store and access data, but they can also be vulnerable to malicious attacks. Hackers can use RFID scanners to steal money from your . A small chip -- known as an RFID tag -- is attached to or implanted in an object. The tags contain information that can be read at short range via radio waves. The chip and .
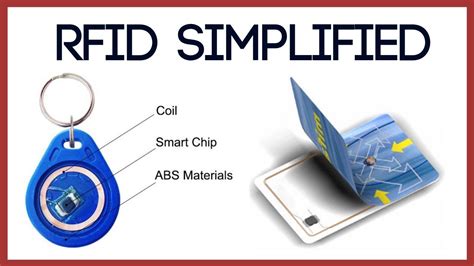
Identity thieves could read the same information from an RFID-enabled passport, or a security access card with an RFID chip. In 2006, a Dutch passport was read from ten .
Despite its widespread application and usage, RFID poses security threats and challenges that need to be addressed properly before deployment. This post aims to highlight several . An introduction to RFID security. 21 July 2023. This blog is intended for individuals with a technical background eager to explore Radio Frequency IDentification (RFID) .
You probably know that the embedded computer chips found in most credit and debit cards are meant to protect you from financial fraud. But you may have also heard of a .
The main security issue associated with the use of RFID systems is that they are susceptible to attacks or viruses from hackers and fraudsters. However, there is comfort in . This bulletin provides an overview of RFID technologies and recommends practices for initiating, designing, implementing, and operating RFID systems in a manner that .Implementing robust security practices is crucial for safeguarding RFID systems against potential attacks. Here are some key best practices: Encrypt RFID Data: Encrypting the data .
This publication seeks to assist organizations in understanding the risks of RFID technology and security measures to mitigate those risks. It provides practical, real-world . RFID chips are a convenient way to store and access data, but they can also be vulnerable to malicious attacks. Hackers can use RFID scanners to steal money from your . A small chip -- known as an RFID tag -- is attached to or implanted in an object. The tags contain information that can be read at short range via radio waves. The chip and .
Identity thieves could read the same information from an RFID-enabled passport, or a security access card with an RFID chip. In 2006, a Dutch passport was read from ten .Despite its widespread application and usage, RFID poses security threats and challenges that need to be addressed properly before deployment. This post aims to highlight several . An introduction to RFID security. 21 July 2023. This blog is intended for individuals with a technical background eager to explore Radio Frequency IDentification (RFID) .
You probably know that the embedded computer chips found in most credit and debit cards are meant to protect you from financial fraud. But you may have also heard of a . The main security issue associated with the use of RFID systems is that they are susceptible to attacks or viruses from hackers and fraudsters. However, there is comfort in .
This bulletin provides an overview of RFID technologies and recommends practices for initiating, designing, implementing, and operating RFID systems in a manner that .Implementing robust security practices is crucial for safeguarding RFID systems against potential attacks. Here are some key best practices: Encrypt RFID Data: Encrypting the data .
where are rfid chips used
types of rfid chips
rfid chips in humans
I know I need a reader for the 2DS, but I don't know if it has to be the Nintendo reader or it can .
rfid chips secuirty|pros and cons of rfid