smart cards authentication protocol This topic for the IT professional describes the system architecture that supports smart cards in the Windows operating system, including credential provider architecture and the smart card subsystem architecture. Authentication is a process for verifying the identity of . What are the Best NFC Business Cards? After hours of research and trials, here is my list of the top NFC cards on the market. QUick Links – Best digital business cards. Popl – Best Overall. Mobilo – Great for Teams. Linq – Great for Solopreneurs. Wave – All the Essentials. Blinq – Minimalistic Owners. V1Ce – Awesome Phone Cases.
0 · smart card multi factor authentication
1 · smart card identity
2 · smart card based identification system
3 · smart card authentication step by
4 · smart card authentication protocol
5 · enable smart card log on
6 · enable smart card authentication
7 · authenticate using your smart card
NFC Business Cards+. We have discontinued our NFC Business Cards+ as of .Popular business card maker launches NFC app to write to upcoming NFC cards. By BrothaTech. February 22, 2013. MOO.com is known .
Vendors provide smart cards and smart card readers, and in many cases the vendors are different for the smart card and the smart card reader. Drivers for smart . See more Smart cards can be used to sign in to domain accounts only, not local accounts. When you use a password to sign in interactively to a domain account, Windows uses the .This topic for the IT professional describes the system architecture that supports smart cards in the Windows operating system, including credential provider architecture and the smart card subsystem architecture. Authentication is a process for verifying the identity of . Smart cards can be used to sign in to domain accounts only, not local accounts. When you use a password to sign in interactively to a domain account, Windows uses the Kerberos version 5 (v5) protocol for authentication.
The YubiKey NEO device10 from Yubico supports multiple authentication protocols including the FIDO Alliance U2F protocol, one-time password, and smart card functionality (e.g., OpenPGP, the Federal government’s Personal Identity Verification (PIV) credential).Smart cards serve as credit or ATM cards, fuel cards, mobile phone SIMs, authorization cards for pay television, household utility pre-payment cards, high-security identification and access badges, and public transport and public phone payment cards. Learn how 1Kosmos enhances smart card authentication with BlockID, offering biometric-based security, identity proofing, privacy by design, distributed ledger technology, interoperability, and industry certifications.How Smart Card Sign-in Works in Windows. Article 10/29/2024 11 contributors Applies to: Windows 11, Windows 10, Windows Server 2025, Windows Server 2022, Windows Server 2019, Windows Server 2016. Feedback.
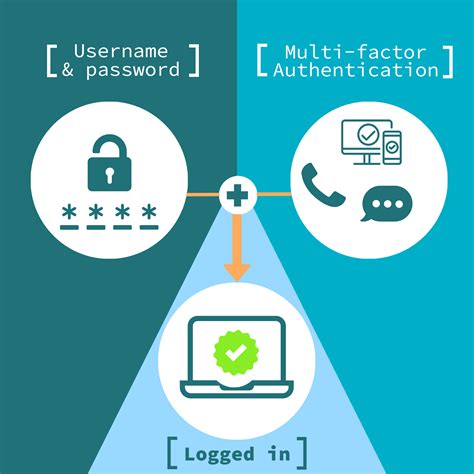
This section describes what a smart card is and how smart card authentication works. It describes the tools that you can use to read and manipulate smart card content. It also provides sample use cases and describes the setup of both the IdM server and IdM client for smart card authentication. Authentication Steps: The user puts the smart card into a card reader hooked up to the device or system they want to use. The card reader talks to the smart card and asks the user to enter a password number or use their body marks to prove who they are.Smart Card Authentication is a means of verifying users into enterprise resources such as workstations and applications using a physical card in tandem with a smart card reader and software on the workstation. Smart card authentication is a method that employs the embedded chip in the card to verify the identity of the user certificates. The chip can generate or store authentication data through cryptographic algorithms that a reader can verify.
This topic for the IT professional describes the system architecture that supports smart cards in the Windows operating system, including credential provider architecture and the smart card subsystem architecture. Authentication is a process for verifying the identity of . Smart cards can be used to sign in to domain accounts only, not local accounts. When you use a password to sign in interactively to a domain account, Windows uses the Kerberos version 5 (v5) protocol for authentication.
The YubiKey NEO device10 from Yubico supports multiple authentication protocols including the FIDO Alliance U2F protocol, one-time password, and smart card functionality (e.g., OpenPGP, the Federal government’s Personal Identity Verification (PIV) credential).Smart cards serve as credit or ATM cards, fuel cards, mobile phone SIMs, authorization cards for pay television, household utility pre-payment cards, high-security identification and access badges, and public transport and public phone payment cards. Learn how 1Kosmos enhances smart card authentication with BlockID, offering biometric-based security, identity proofing, privacy by design, distributed ledger technology, interoperability, and industry certifications.How Smart Card Sign-in Works in Windows. Article 10/29/2024 11 contributors Applies to: Windows 11, Windows 10, Windows Server 2025, Windows Server 2022, Windows Server 2019, Windows Server 2016. Feedback.
This section describes what a smart card is and how smart card authentication works. It describes the tools that you can use to read and manipulate smart card content. It also provides sample use cases and describes the setup of both the IdM server and IdM client for smart card authentication. Authentication Steps: The user puts the smart card into a card reader hooked up to the device or system they want to use. The card reader talks to the smart card and asks the user to enter a password number or use their body marks to prove who they are.Smart Card Authentication is a means of verifying users into enterprise resources such as workstations and applications using a physical card in tandem with a smart card reader and software on the workstation.
how to block rfid readers
smart card multi factor authentication
smart card identity
smart card based identification system

With an EMV card, the small EMV chip ensures a stolen card isn't being used. EMV cards can be contactless and use the same kind of technology that enables NFC to be processed without any physical touching. Sensitive information can .
smart cards authentication protocol|smart card authentication step by