rfid authentication system An RFID access control system is a security management system based on radio frequency identification technology, designed to control and manage personnel access to specific areas. The system achieves contactless access control by identifying users carrying RFID tags and is widely used in enterprises, schools, hospitals, and other locations. Dimensions: Length: 5.05 inches. Width: 1.5 inches. Height: 1.6 inches. Give your Amiibo card collection the perfect home with this 3D printed Amiibo NFC card storage box. Order yours today and keep your cards safe, .
0 · rfid authentication software
1 · rfid authentication
2 · hid rfid support
3 · hid rfid authentication
4 · hid rfid
Card emulation with a secure element. When NFC card emulation is provided using a secure element, the card to be emulated is provisioned into the secure element on the device through an Android application. Then, when .
rfid authentication software
RFID-powered authentication gives users easy access to business systems they need — and nothing they don’t — with a single, simple credential. Connected Workplace. Access Everywhere.
An RFID access control system is a security management system based on radio frequency identification technology, designed to control and manage personnel access to specific areas. . There exists a variety of RFID-based authentication schemes for safeguarding RFID systems from various security and privacy attacks. These schemes are typically based on .RFID-powered authentication gives users easy access to business systems they need — and nothing they don’t — with a single, simple credential. Connected Workplace. Access Everywhere.
smart card programmer usb
rfid authentication
An RFID access control system is a security management system based on radio frequency identification technology, designed to control and manage personnel access to specific areas. The system achieves contactless access control by identifying users carrying RFID tags and is widely used in enterprises, schools, hospitals, and other locations.
There exists a variety of RFID-based authentication schemes for safeguarding RFID systems from various security and privacy attacks. These schemes are typically based on traditional lightweight cryptographic primitives, for instance, symmetric key encryption and one-way hash functions.Commodity ultra-high-frequency (UHF) RFID authentication systems only provide weak user authentication, as RFID tags can be easily stolen, lost, or cloned by attackers. This paper presents the design and evaluation of SmartRFID, a novel UHF RFID authentication system to promote commodity crypto-less UHF RFID tags for security-sensitive . Very recently, Gope and Hwang proposed an authentication protocol for RFID systems based on only lightweight primitives and claimed their protocol can withstand all known attacks. However, as per the analysis in this article, their protocol is infeasible and is vulnerable to collision, denial-of-service (DoS), and stolen verifier attacks. We propose RF-Ubia, a low-cost user authentication system that utilizes commodity low-cost RFID devices to authenticate based on the user’s biometric characteristics. In this work, we take into account different population groups where users can authenticate with or without passwords.
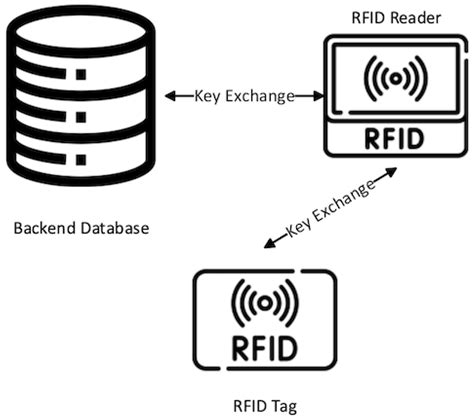
To overcome the limitations of the existing schemes and to achieve both security and efficiency together for the IoT, we introduce a novel and efficient RFID authentication protocol-based Elliptic Curve Cryptography (ECC) to maintain security between RFID cards, card readers, and servers.
In an RFID system, security and privacy are considered two main concerns. Considering these problems, we proposed an efficient and reliable ultralightweight RFID authentication scheme (E R 2 AS) for healthcare systems to enhance patients’ medication safety. However, the RFID techniques are plagued to security and privacy issues due to underlying wireless communication channel. In order to come up with a solution, we propose an efficient authentication scheme which uses pseudorandom number generators (PRNG) and some simple cryptographic operations. Liu et al. proposed an authentication protocol for an RFID system by using hash and XoR operations. The correctness of the protocol was proven by using “Burrows–Abadi–Needham (BAN)” logic analysis.
RFID-powered authentication gives users easy access to business systems they need — and nothing they don’t — with a single, simple credential. Connected Workplace. Access Everywhere.An RFID access control system is a security management system based on radio frequency identification technology, designed to control and manage personnel access to specific areas. The system achieves contactless access control by identifying users carrying RFID tags and is widely used in enterprises, schools, hospitals, and other locations. There exists a variety of RFID-based authentication schemes for safeguarding RFID systems from various security and privacy attacks. These schemes are typically based on traditional lightweight cryptographic primitives, for instance, symmetric key encryption and one-way hash functions.
smart card pop up windows 10
Commodity ultra-high-frequency (UHF) RFID authentication systems only provide weak user authentication, as RFID tags can be easily stolen, lost, or cloned by attackers. This paper presents the design and evaluation of SmartRFID, a novel UHF RFID authentication system to promote commodity crypto-less UHF RFID tags for security-sensitive .
Very recently, Gope and Hwang proposed an authentication protocol for RFID systems based on only lightweight primitives and claimed their protocol can withstand all known attacks. However, as per the analysis in this article, their protocol is infeasible and is vulnerable to collision, denial-of-service (DoS), and stolen verifier attacks.
We propose RF-Ubia, a low-cost user authentication system that utilizes commodity low-cost RFID devices to authenticate based on the user’s biometric characteristics. In this work, we take into account different population groups where users can authenticate with or without passwords.
To overcome the limitations of the existing schemes and to achieve both security and efficiency together for the IoT, we introduce a novel and efficient RFID authentication protocol-based Elliptic Curve Cryptography (ECC) to maintain security between RFID cards, card readers, and servers. In an RFID system, security and privacy are considered two main concerns. Considering these problems, we proposed an efficient and reliable ultralightweight RFID authentication scheme (E R 2 AS) for healthcare systems to enhance patients’ medication safety. However, the RFID techniques are plagued to security and privacy issues due to underlying wireless communication channel. In order to come up with a solution, we propose an efficient authentication scheme which uses pseudorandom number generators (PRNG) and some simple cryptographic operations.

hid rfid support
Altex.ro va ofera o gama larga de carduri de memorie pentru aparate foto sau telefoane mobile de la cele mai cautate branduri: Sandisk, Hama, Addlink. Profita acum de preturile mici! . Card de memorie SAMSUNG PRO Plus, .
rfid authentication system|hid rfid authentication