rfid fraud sensor If hackers access or steal the data that RFID technology captures, they could exploit it to commit crimes like financial or medical fraud or identity theft. Here are a several things you need to know about RFID technology. The ReadID Me app (previously known as NFC Passport Reader) reads and verifies the NFC chip embedded in electronic passports, national identity cards and other ICAO compliant identity documents (ePassport, or, in .
0 · rfid sensor simulation
1 · rfid sensor price
2 · rfid sensor meaning
3 · rfid sensor full form
4 · rfid sensor datasheet
5 · rfid sensor cost
6 · rfid is involved when using
7 · rfid full form in computer
First of all, you need the keys for the tag you want to read. Due to some .
With the recent shift to contactless payment cards, more cybercriminals are turning to RFID credit card theft via scanning. This article will explain how this theft happens and provide tips on how to protect your RFID credit card from .With the recent shift to contactless payment cards, more cybercriminals are turning to RFID credit card theft via scanning. This article will explain how this theft happens and provide tips on how to protect your RFID credit card from potential thefts and other common payment card frauds. You probably know that the embedded computer chips found in most credit and debit cards are meant to protect you from financial fraud. But you may have also heard of a scam called RFID skimming, where a thief steals the card number from your chip-embedded card just by walking past you.RFID skimming is a method to unlawfully obtain someone's payment card information using a RFID reading device. How RFID skimming is performed. Modern payment cards have a built in chip that transmits card information wirelessly.
If hackers access or steal the data that RFID technology captures, they could exploit it to commit crimes like financial or medical fraud or identity theft. Here are a several things you need to know about RFID technology.
A skimmer is a device installed on card readers that collec ts card numbers. Thieves will later recover and use this information to make fraudulent purchases. Skimmers are not usually spotted.
Item tags, such as RFID (radio-frequency identification) tags, can provide retailers with essential data on what was taken, when and via which exit. These data can be analyzed to determine if the theft was internal or external, find shoplifting patterns, predict future theft and update the retailer’s inventory view.
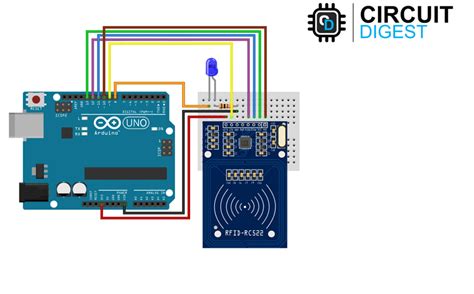
Despite demonstrations to show it's possible, documented cases of RFID credit card fraud are unknown. And as security professionals know, there is a huge gulf between potential crime and actual.RFID anti-theft systems are theft-prevention technology used in retailing and warehousing to identify and track inventory in real-time. The technology includes RFID tags attached to items, RFID readers that detect the tags if not deactivated, an alarm, and a database/software system for processing and storing data and information.
RFID provides retailers with a host of new applications that reduce losses, track items throughout the supply chain and improve inventory accuracy. The NRF found that retailers suffer as much as 1.6 percent shrink (the term used for lost inventory) annually.Wireless identity theft, also known as contactless identity theft or RFID identity theft, is a form of identity theft described as "the act of compromising an individual’s personal identifying information using wireless (radio frequency) mechanics."
With the recent shift to contactless payment cards, more cybercriminals are turning to RFID credit card theft via scanning. This article will explain how this theft happens and provide tips on how to protect your RFID credit card from potential thefts and other common payment card frauds.
You probably know that the embedded computer chips found in most credit and debit cards are meant to protect you from financial fraud. But you may have also heard of a scam called RFID skimming, where a thief steals the card number from your chip-embedded card just by walking past you.RFID skimming is a method to unlawfully obtain someone's payment card information using a RFID reading device. How RFID skimming is performed. Modern payment cards have a built in chip that transmits card information wirelessly. If hackers access or steal the data that RFID technology captures, they could exploit it to commit crimes like financial or medical fraud or identity theft. Here are a several things you need to know about RFID technology.
A skimmer is a device installed on card readers that collec ts card numbers. Thieves will later recover and use this information to make fraudulent purchases. Skimmers are not usually spotted. Item tags, such as RFID (radio-frequency identification) tags, can provide retailers with essential data on what was taken, when and via which exit. These data can be analyzed to determine if the theft was internal or external, find shoplifting patterns, predict future theft and update the retailer’s inventory view. Despite demonstrations to show it's possible, documented cases of RFID credit card fraud are unknown. And as security professionals know, there is a huge gulf between potential crime and actual.
RFID anti-theft systems are theft-prevention technology used in retailing and warehousing to identify and track inventory in real-time. The technology includes RFID tags attached to items, RFID readers that detect the tags if not deactivated, an alarm, and a database/software system for processing and storing data and information. RFID provides retailers with a host of new applications that reduce losses, track items throughout the supply chain and improve inventory accuracy. The NRF found that retailers suffer as much as 1.6 percent shrink (the term used for lost inventory) annually.
how many wild cards are there in the nfc
Try the Tag Reader in Control Center. If your iPhone isn’t automatically recognizing NFC tags, you can try using the NFC Tag Reader tool that’s built into your iPhone. However, this is only .
rfid fraud sensor|rfid full form in computer