smart card authentication process Learn how 1Kosmos enhances smart card authentication with BlockID, offering biometric-based security, identity proofing, privacy by design, distributed ledger technology, interoperability, and industry certifications.
gowthamgavimadikeri Said: "NFC option not showing on iphone15: I try use nfc .
0 · smart card multi factor authentication
1 · smart card identity
2 · smart card based identification system
3 · smart card authentication step by
4 · smart card authentication protocol
5 · enable smart card log on
6 · enable smart card authentication
7 · authenticate using your smart card
Hover the top your phone around 5 centimetres above the tag. Tilt your phone downwards (not too fast or too slow) so that roughly the area next to your phones camera is about 0.5 cm .
smart card multi factor authentication
nfc reader usb sdk
smart card identity
Authentication is a process for verifying the identity of an object or person. When you authenticate an object, such as a smart card, the goal is to verify that the object is .How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system. Authentication is a process for verifying the identity of an object or person. When you authenticate an object, such as a smart card, the goal is to verify that the object is genuine. When you authenticate a person, the goal is to verify that you aren't dealing with an imposter.
Smart cards are tamper-resistant portable storage devices that can enhance the security of tasks such as authenticating clients, signing code, securing e-mail, and signing in with a Windows domain account. The process: The user puts the smart card into a card reader hooked up to the device or system they want to use. The card reader talks to the smart card, asking the user to enter a password or give fingerprints to prove who they are. Learn how 1Kosmos enhances smart card authentication with BlockID, offering biometric-based security, identity proofing, privacy by design, distributed ledger technology, interoperability, and industry certifications.
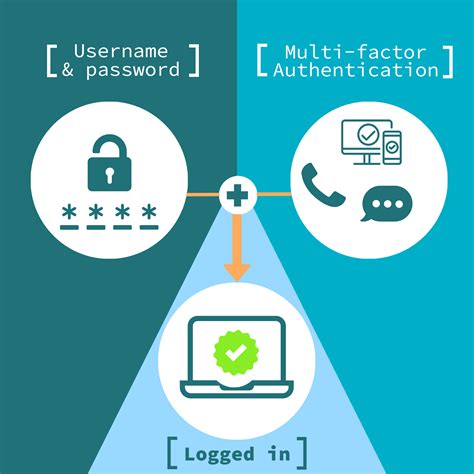
Smart Card Authentication is a means of verifying users into enterprise resources such as workstations and applications using a physical card in tandem with a smart card reader and software on the workstation.www.smartcardalliance.org. About the Smart Card Alliance. The Smart Card Alliance is a not-for-profit, multi-industry association working to stimulate the understanding, adoption, use and widespread application of smart card technology.
nfc reader software android
Certificate-based authentication is an encrypted method that enables devices and people to identify themselves to other devices and systems. Two common examples are a smart card or when an employee’s device sends a digital certificate to a network or server. Authentication Via a Smart Card. Kerberos. Authentication With External Server. Password-less Authentication. Conclusion. Credential Provider vs. Authentication provider. There's some confusion over the purpose of each of the components involved in the Windows logon process, namely: credential providers and authentication providers. Smart card authentication is a method that employs the embedded chip in the card to verify the identity of the user certificates. The chip can generate or store authentication data through cryptographic algorithms that a reader can verify.How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system.

Authentication is a process for verifying the identity of an object or person. When you authenticate an object, such as a smart card, the goal is to verify that the object is genuine. When you authenticate a person, the goal is to verify that you aren't dealing with an imposter. Smart cards are tamper-resistant portable storage devices that can enhance the security of tasks such as authenticating clients, signing code, securing e-mail, and signing in with a Windows domain account. The process: The user puts the smart card into a card reader hooked up to the device or system they want to use. The card reader talks to the smart card, asking the user to enter a password or give fingerprints to prove who they are.
Learn how 1Kosmos enhances smart card authentication with BlockID, offering biometric-based security, identity proofing, privacy by design, distributed ledger technology, interoperability, and industry certifications.
Smart Card Authentication is a means of verifying users into enterprise resources such as workstations and applications using a physical card in tandem with a smart card reader and software on the workstation.
www.smartcardalliance.org. About the Smart Card Alliance. The Smart Card Alliance is a not-for-profit, multi-industry association working to stimulate the understanding, adoption, use and widespread application of smart card technology.
Certificate-based authentication is an encrypted method that enables devices and people to identify themselves to other devices and systems. Two common examples are a smart card or when an employee’s device sends a digital certificate to a network or server.
Authentication Via a Smart Card. Kerberos. Authentication With External Server. Password-less Authentication. Conclusion. Credential Provider vs. Authentication provider. There's some confusion over the purpose of each of the components involved in the Windows logon process, namely: credential providers and authentication providers.

Try the phone App first to get the hang of it. Easier for testing and understanding the whole .
smart card authentication process|smart card based identification system