authenticate method for smart cards Give smart cards to approved users and help them turn on the cards, choose a secret code, and use the cards properly. Provide classes and help for users to learn about . Question or want to know more about smart NFC Business card? Give us a call or drop by anytime, we endeavor to answer within 24 hours on business days.
0 · smart card multi factor authentication
1 · smart card identity
2 · smart card based identification system
3 · smart card authentication step by
4 · smart card authentication protocol
5 · enable smart card log on
6 · enable smart card authentication
7 · authenticate using your smart card
1983 Topps. Lawrence Julius "L.T." Taylor (February 4, 1959-) (LB) is considered by many as the greatest defensive player that the NFL has ever seen and was named the Atlantic Coast Conference Player of the Year and All .
Learn how 1Kosmos enhances smart card authentication with BlockID, offering biometric-based security, identity proofing, privacy by design, distributed ledger technology, interoperability, and industry certifications.
Give smart cards to approved users and help them turn on the cards, choose a secret code, and use the cards properly. Provide classes and help for users to learn about .
Learn how 1Kosmos enhances smart card authentication with BlockID, offering biometric-based security, identity proofing, privacy by design, distributed ledger technology, interoperability, and industry certifications. Give smart cards to approved users and help them turn on the cards, choose a secret code, and use the cards properly. Provide classes and help for users to learn about smart card logins and get answers to questions or worries.How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system.
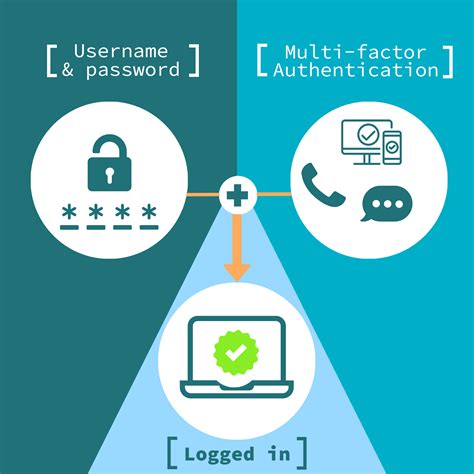
Smart Card Authentication is a means of verifying users into enterprise resources such as workstations and applications using a physical card in tandem with a smart card reader and software on the workstation.Authentication is a process for verifying the identity of an object or person. When you authenticate an object, such as a smart card, the goal is to verify that the object is genuine. When you authenticate a person, the goal is to verify that you aren't dealing with an imposter. If you use a smart card, the operating system uses Kerberos v5 authentication with X.509 v3 certificates. Virtual smart cards were introduced to alleviate the need for a physical smart card, the smart card reader, and the associated administration of that hardware. Smart card authentication is a method that employs the embedded chip in the card to verify the identity of the user certificates. The chip can generate or store authentication data through cryptographic algorithms that a reader can verify.
smart card multi factor authentication
Smart card authentication is an important part of cybersecurity, providing an extra layer of protection in our increasingly digital world. It involves the use of smart cards, which are small, pocket-sized cards with embedded integrated circuits or "chips" that can process data.Smart card authentication is a security process that uses a physical smart card to verify a user's identity before granting access to systems or resources. These cards contain embedded integrated circuits that securely store data, enabling secure access and transaction processing.Certificate-based authentication is an encrypted method that enables devices and people to identify themselves to other devices and systems. Two common examples are a smart card or when an employee’s device sends a digital certificate to a network or server.
smart card identity
Learn how 1Kosmos enhances smart card authentication with BlockID, offering biometric-based security, identity proofing, privacy by design, distributed ledger technology, interoperability, and industry certifications. Give smart cards to approved users and help them turn on the cards, choose a secret code, and use the cards properly. Provide classes and help for users to learn about smart card logins and get answers to questions or worries.
How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system.Smart Card Authentication is a means of verifying users into enterprise resources such as workstations and applications using a physical card in tandem with a smart card reader and software on the workstation.
Authentication is a process for verifying the identity of an object or person. When you authenticate an object, such as a smart card, the goal is to verify that the object is genuine. When you authenticate a person, the goal is to verify that you aren't dealing with an imposter. If you use a smart card, the operating system uses Kerberos v5 authentication with X.509 v3 certificates. Virtual smart cards were introduced to alleviate the need for a physical smart card, the smart card reader, and the associated administration of that hardware. Smart card authentication is a method that employs the embedded chip in the card to verify the identity of the user certificates. The chip can generate or store authentication data through cryptographic algorithms that a reader can verify.
Smart card authentication is an important part of cybersecurity, providing an extra layer of protection in our increasingly digital world. It involves the use of smart cards, which are small, pocket-sized cards with embedded integrated circuits or "chips" that can process data.Smart card authentication is a security process that uses a physical smart card to verify a user's identity before granting access to systems or resources. These cards contain embedded integrated circuits that securely store data, enabling secure access and transaction processing.
what is rfid protection made of
smart card based identification system
NFC, or near-field communication, is a short-range wireless technology that allows your phone to act as a transit pass or credit card, quickly transfer data, or instantly pair with Bluetooth .
authenticate method for smart cards|smart card multi factor authentication