stealing credit card numbers using rfid With contactless payments, thieves can use radio frequency identification (RFID) technology to skim your card’s information if they’re close enough to the card reader. How to protect yourself: Use RFID-blocking wallets or cases .
Anyone ever purchased BOTW NFC game cards? Never owned an amiibo before, but starting .
0 · rfid embedded credit cards
1 · rfid credit card security tips
2 · rfid credit card security
3 · rfid credit card scam
4 · rfid credit card history
5 · rfid card fraud
6 · how to protect rfid credit cards
7 · are rfid credit cards safe
That’s how easy it is to copy or clone an access card or RFID key fob. How to copy HID cards and get them on your phone. People ask questions like: “How can a mobile’s NFC be used as an HID proximity card (used at the .3. Tap and pay at checkout. You can pay with your phone in stores anywhere you see the contactless symbol. To use your phone to make a payment, just tap or hold your device over the card reader and wait until you see a check mark or a “done” icon to confirm the .
People often discover their credit card numbers have been stolen by receiving a transaction notification or bank statement showing an unfamiliar transaction. If your card is still with you, it’s possible someone obtained your information . Some security experts have voiced concerns about a phenomenon called RFID skimming, in which a thief with an RFID reader may be able to steal your credit card number or personal information simply by walking within a few feet of you.People often discover their credit card numbers have been stolen by receiving a transaction notification or bank statement showing an unfamiliar transaction. If your card is still with you, it’s possible someone obtained your information while you were using the card or via an RFID reader. In 2015, security researchers were able to wirelessly steal RFID credit card information (e.g., account numbers and expiration dates) from closely held, unobstructed cards and re-use them.
Use a temporary credit card for online shopping. Many banks and credit companies will offer this service for no fee. You can get a card number that is separate from your actual account, but the bank links it to your account for your bona fide purchases. With contactless payments, thieves can use radio frequency identification (RFID) technology to skim your card’s information if they’re close enough to the card reader. How to protect yourself: Use RFID-blocking wallets or cases .
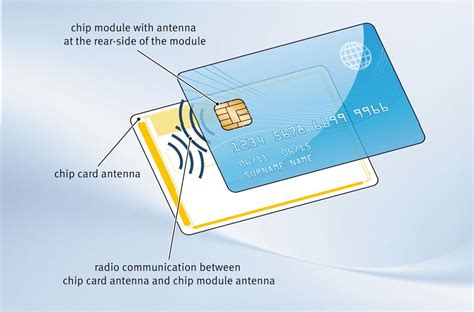
RFID skimming is a method to unlawfully obtain someone's payment card information using a RFID reading device. How RFID skimming is performed. Modern payment cards have a built in chip that transmits card information wirelessly. RFID theft is a misunderstood risk associated with modern technology. While it is theoretically possible to steal someone’s card information using RFID skimmers, the data they get would be missing the necessary identifiers to carry out large scale fraud or in most cases even a simple transaction.
Updated: Oct 21, 2024, 2:21pm. Editorial Note: We earn a commission from partner links on Forbes Advisor. Commissions do not affect our editors' opinions or evaluations. Getty. Card skimming.Skimming occurs when devices illegally installed on or inside ATMs, point-of-sale (POS) terminals, or fuel pumps capture card data and record cardholders’ PIN entries. RFID credit cards are considered safe to use, and credit card fraud using RFID readers is rare and difficult to do.
Some security experts have voiced concerns about a phenomenon called RFID skimming, in which a thief with an RFID reader may be able to steal your credit card number or personal information simply by walking within a few feet of you.People often discover their credit card numbers have been stolen by receiving a transaction notification or bank statement showing an unfamiliar transaction. If your card is still with you, it’s possible someone obtained your information while you were using the card or via an RFID reader. In 2015, security researchers were able to wirelessly steal RFID credit card information (e.g., account numbers and expiration dates) from closely held, unobstructed cards and re-use them.
Use a temporary credit card for online shopping. Many banks and credit companies will offer this service for no fee. You can get a card number that is separate from your actual account, but the bank links it to your account for your bona fide purchases. With contactless payments, thieves can use radio frequency identification (RFID) technology to skim your card’s information if they’re close enough to the card reader. How to protect yourself: Use RFID-blocking wallets or cases .

RFID skimming is a method to unlawfully obtain someone's payment card information using a RFID reading device. How RFID skimming is performed. Modern payment cards have a built in chip that transmits card information wirelessly.
RFID theft is a misunderstood risk associated with modern technology. While it is theoretically possible to steal someone’s card information using RFID skimmers, the data they get would be missing the necessary identifiers to carry out large scale fraud or in most cases even a simple transaction.Updated: Oct 21, 2024, 2:21pm. Editorial Note: We earn a commission from partner links on Forbes Advisor. Commissions do not affect our editors' opinions or evaluations. Getty. Card skimming.Skimming occurs when devices illegally installed on or inside ATMs, point-of-sale (POS) terminals, or fuel pumps capture card data and record cardholders’ PIN entries.
rfid embedded credit cards
rfid credit card security tips

Click the menu (3 lines) icon in the top left of the title bar. Enable Power Tag support in the Tag Devices section. Select or scan the desired item to open the amiibo™ preview. Use the .
stealing credit card numbers using rfid|how to protect rfid credit cards