flaws of rfid tags RFID Counterfeiting: depending on the computing power, RFID can be classified into three categories: See more What is NFC technology? Near Field Communication or NFC are short range transmissions that require devices to be in close proximity. This technology allows u.
0 · sniffing rfid
1 · rfid tracking
2 · rfid tags
3 · rfid security threats
4 · rfid security problems
5 · rfid mythology
6 · rfid misconceptions
7 · myths about rfid
Basic reboots, NFC settings checks, case removal and device unlocking are good starting points. When that fails, cache clearing, software updates, even factory resets could get your NFC payments functioning again. .
Like any other security devices and mechanism RFID is not flawless. Despite its widespread application and usage, RFID poses security threats and challenges that need to be addressed properly before deployment. This post aims to highlight several important RFID related security issues. Like any other . See more
iogear smart card reader software for mac
RFID Counterfeiting: depending on the computing power, RFID can be classified into three categories: See moreIn a spoofing attack, the attacker masquerade as a legitimate user of the system. The attacker can pose himself as an authorized Object Naming Service user or database user. If an attacker can successfully get access to the system with his spoofed . See moreIn this type of attack, an attacker tries to insert system commands to the RFID system instead of sending normal data.an example of RFID insert attack is that a tag carrying system . See more
As you know that repudiation means when as user officially deny that he has done an action and we have no way to verify that whether he has performed that particular action. In the case of . See moreAn RFID virus can either destroy or disclose the tags data stored in the database disrupt the service or block the communication between the database and the reader. To protect your RIFD database, make sure you mitigate database related vulnerabilities and risks. Myth #1: RFID Is Only for Big Organizations. RFID technology provides the most efficient and accurate way for organizations to track, trace, and monitor assets, and enterprises of all sizes can benefit from the improved asset visibility and management facilitated by RFID.
Security of RFID Tags. Security of passive RFID tags is also considered as one of the major challenges in RFID field. There are many unguarded passive tags that can be exposed to malevolent and spiteful attacks, including spoofing, eavesdropping, denial of service.
RFID badges in access control face serious shortcomings. Near field communication (NFC) is a newer technology, comparable to RFID. Most modern smartphones are equipped with NFC tags. Consequently, smartphones can communicate with door readers, making RFID badges obsolete.
By closely monitoring the power consumption levels of RFID tags, hackers can fool your systems. With some ingenuity and a cell phone bad actors can perform an RFID hack that will steal sensitive information or breach secured areas.
Besides being vulnerable to common attacks such as eavesdropping, man-in-the-middle, and denial of service, RFID technology is, in particular, susceptible to spoofing and power attacks (Figure 2). This section illustrates different kinds of attacks and provides countermeasures against these attacks. Fig. 2. Six RFID Trends for 2021 and Beyond. According to a recent RFID market report, the global market for RFID tags, readers and software is expected to reach .7 billion this year and expand to .4 billion by 2026. Here are some of the trends driving that growth.RFID Labels Explore radio-frequency identification (RFID) asset tags. Labels that meet defense standards and last the life of your assets. Track property, manage preventive maintenance, reduce operational costs, and more with UID labels that meet an array of government, industrial and military specifications including MIL-STD 130.
Security issues in RFID system. The RFID scheme consists of several classes of tags and reader. These tags include an inadequate amount of memory and low-power capacity. However, there are numerous other issues in terms of . In a paper posted at www.rfidanalysis.org, the researchers claim that by cracking a proprietary cipher, or encryption algorithm in one of TI’s DST (digital signature transponder) RFID tags, they were able to circumvent the tags’ built-in security enough to buy gasoline and turn on a .
An RFID virus can either destroy or disclose the tags data stored in the database disrupt the service or block the communication between the database and the reader. To protect your RIFD database, make sure you mitigate database related vulnerabilities and risks. Myth #1: RFID Is Only for Big Organizations. RFID technology provides the most efficient and accurate way for organizations to track, trace, and monitor assets, and enterprises of all sizes can benefit from the improved asset visibility and management facilitated by RFID.Security of RFID Tags. Security of passive RFID tags is also considered as one of the major challenges in RFID field. There are many unguarded passive tags that can be exposed to malevolent and spiteful attacks, including spoofing, eavesdropping, denial of service.RFID badges in access control face serious shortcomings. Near field communication (NFC) is a newer technology, comparable to RFID. Most modern smartphones are equipped with NFC tags. Consequently, smartphones can communicate with door readers, making RFID badges obsolete.
By closely monitoring the power consumption levels of RFID tags, hackers can fool your systems. With some ingenuity and a cell phone bad actors can perform an RFID hack that will steal sensitive information or breach secured areas.
Besides being vulnerable to common attacks such as eavesdropping, man-in-the-middle, and denial of service, RFID technology is, in particular, susceptible to spoofing and power attacks (Figure 2). This section illustrates different kinds of attacks and provides countermeasures against these attacks. Fig. 2.
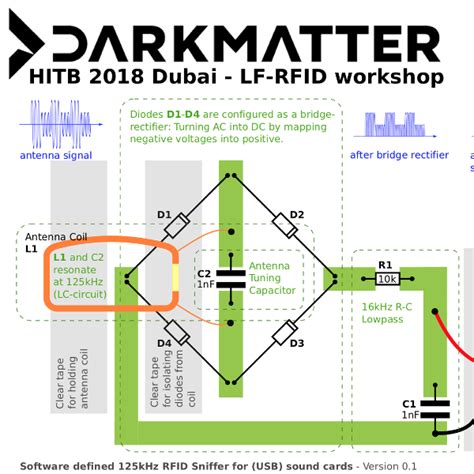
sniffing rfid
Six RFID Trends for 2021 and Beyond. According to a recent RFID market report, the global market for RFID tags, readers and software is expected to reach .7 billion this year and expand to .4 billion by 2026. Here are some of the trends driving that growth.RFID Labels Explore radio-frequency identification (RFID) asset tags. Labels that meet defense standards and last the life of your assets. Track property, manage preventive maintenance, reduce operational costs, and more with UID labels that meet an array of government, industrial and military specifications including MIL-STD 130. Security issues in RFID system. The RFID scheme consists of several classes of tags and reader. These tags include an inadequate amount of memory and low-power capacity. However, there are numerous other issues in terms of .
rfid tracking
NDEF reader/writer tool for Windows, Mac and Linux Desktop PCs for NXP NFC ICs. Similar to .
flaws of rfid tags|rfid misconceptions