rf security tag removal Learn how to safely remove RFID stickers with our step-by-step guide. Protect your privacy and prevent unwanted tracking with our proven methods. Multi-purpose NFC readers for consumer and industrial . High-volume, mass .
0 · removing rfid stickers
1 · how do am security tags work
2 · am security tag deactivation
3 · am and rf security tags
To use NFC Tools - NFC Tag Reader, you have just to hold a tag or a card against the back of your device to read it. NFC Reader lets you copy the content of the tag and copy the tag to infinity with more than one NFC Tags. .
removing rfid stickers
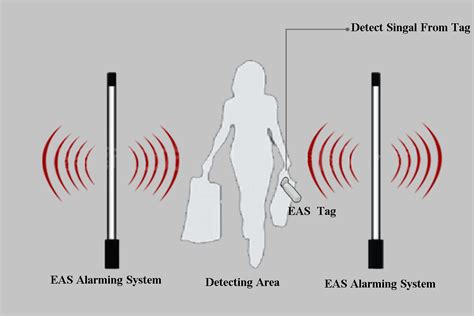
Showing how AM (Acousto magnetic and RF (radio frequency) anti shoplifting tags work and how they are deactivated.Sensormatic Solutions portfolio of power, handheld, and magnetic detachers allow for quick and efficient removal of hard tags from protected merchandise at the POS. Detachers are available .Showing how AM (Acousto magnetic and RF (radio frequency) anti shoplifting tags work and how they are deactivated.Sensormatic Solutions portfolio of power, handheld, and magnetic detachers allow for quick and efficient removal of hard tags from protected merchandise at the POS. Detachers are available .
Learn how to safely remove RFID stickers with our step-by-step guide. Protect your privacy and prevent unwanted tracking with our proven methods. To remove a magnetic security tag with a magnet, you will need a strong neodymium magnet and a pair of pliers. First, locate the locking mechanism on the tag and .
rfid chip kopen
When the checkout operator scans an item with an RF tag on them, a mechanism or magnet in the checkout can remove or destroy an RF tag. This allows a person making . The process of deactivating acousto-magnetic and RF tags is crucial for a smooth transition from purchase to exit. For acousto-magnetic tags, deactivation involves sending a . To remove EAS tags, one needs to insert the Superlock detacher into the designated slot and carefully rotate it and the tag is released, allowing for its removal. These . "To remove and deactivate a UHF RFID tag, use the kill password through a handheld reader or remove the tag from the surface and destroy it by passing charge .

The three main types of security tags are magnet remove tags, clamp remove tags, and slide remove tags. Mechanical security tags are secured with a pin or similar mechanical fastening . In today's #pentestips we're checking How to safely and permanently erase an RFID tag with the NFCKill.
Showing how AM (Acousto magnetic and RF (radio frequency) anti shoplifting tags work and how they are deactivated.Sensormatic Solutions portfolio of power, handheld, and magnetic detachers allow for quick and efficient removal of hard tags from protected merchandise at the POS. Detachers are available . Learn how to safely remove RFID stickers with our step-by-step guide. Protect your privacy and prevent unwanted tracking with our proven methods. To remove a magnetic security tag with a magnet, you will need a strong neodymium magnet and a pair of pliers. First, locate the locking mechanism on the tag and .
When the checkout operator scans an item with an RF tag on them, a mechanism or magnet in the checkout can remove or destroy an RF tag. This allows a person making .
The process of deactivating acousto-magnetic and RF tags is crucial for a smooth transition from purchase to exit. For acousto-magnetic tags, deactivation involves sending a .
To remove EAS tags, one needs to insert the Superlock detacher into the designated slot and carefully rotate it and the tag is released, allowing for its removal. These . "To remove and deactivate a UHF RFID tag, use the kill password through a handheld reader or remove the tag from the surface and destroy it by passing charge .The three main types of security tags are magnet remove tags, clamp remove tags, and slide remove tags. Mechanical security tags are secured with a pin or similar mechanical fastening .
how do am security tags work
am security tag deactivation
am and rf security tags
Download. 1.Click Download File, to download the file. 2. When the File .
rf security tag removal|am and rf security tags