are rfid cards encrypted Here are some key measures to secure RFID systems: Strong encryption . The 2023 Auburn football season will introduce several new affiliates as well .
0 · what is rfid security
1 · what is a rfid card
2 · types of rfid cards
3 · rfid encryption
4 · how to use rfid cards
5 · how secure is rfid
6 · how rfid cards work
7 · basics of rfid cards
Try clearing the cache of the NFC service on your Android phone and check if this fixes your issue. Here’s how you can clear the cache of the NFC service on your Android device: Step 1: Open the .
RFID tags (at least "Class 1 Generation 2" tags) are transponders and they're powered by the very RF wave sent to query them. The majority of RFID tags are not encrypted or have any secrets - they act like a barcode does and merely repeat the same information every .

why put rfid chips into food withut our knowledge
Key Considerations For Successfully Safeguarding Your RFID Card. Taking it to the Next Level in RFID Technology: How to Encrypt RFID Data. Alternatives to Traditional RFID Cards. Wrapping Up and My Experience With . Here are some key measures to secure RFID systems: Strong encryption . RFID tags (at least "Class 1 Generation 2" tags) are transponders and they're powered by the very RF wave sent to query them. The majority of RFID tags are not encrypted or have any secrets - they act like a barcode does and merely repeat the same information every time they're queried, in which case they can very easily be cloned.
what is rfid security
No, you shouldn't panic and start smashing your RFID-enabled credit cards and passports with a hammer. RFID is one of the many ways technology makes life more convenient but can lead to new security and privacy problems. Key Considerations For Successfully Safeguarding Your RFID Card. Taking it to the Next Level in RFID Technology: How to Encrypt RFID Data. Alternatives to Traditional RFID Cards. Wrapping Up and My Experience With RFID Cards and Common Applications of .
Here are some key measures to secure RFID systems: Strong encryption algorithms: Implementing strong encryption protocols ensures that the data transmitted between RFID tags and readers is secure and cannot be easily intercepted or decoded by unauthorized parties. Encryption protects against eavesdropping and data tampering.Use encrypted communication protocol: In the communication between the RFID reader and the card, use a secure communication protocol (such as TLS/SSL) to encrypt the data transmission channel. RFID credit cards are considered safe to use, and credit card fraud using RFID readers is rare and difficult to do. Radio-frequency identification (RFID) credit cards have a type of.To address this, various advanced encryption technologies have been applied to RFID chips to prevent data breaches and unauthorized access. This article will explore these encryption technologies in detail and introduce several well-known .
what is a rfid card
types of rfid cards
In short, RFID technology has existed for many decades, but even modern cards can pose a huge vulnerability in your RFID-based security environment if not implemented well. The main risks are that attackers can gain access to your premise through cloning, replaying, relaying and brute-force attacks.
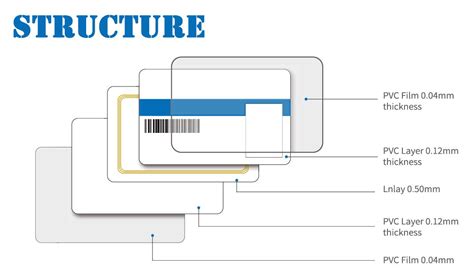
This publication seeks to assist organizations in understanding the risks of RFID technology and security measures to mitigate those risks. It provides practical, real-world advice on how to initiate, design, implement and operate RFID systems in a manner that mitigates security and privacy risks.
The security of RFID cards includes data encryption, access control and anti-counterfeiting technology to ensure the confidentiality and tamper-proofness of information. Some RFID cards use advanced encryption technology such as AES .
RFID tags (at least "Class 1 Generation 2" tags) are transponders and they're powered by the very RF wave sent to query them. The majority of RFID tags are not encrypted or have any secrets - they act like a barcode does and merely repeat the same information every time they're queried, in which case they can very easily be cloned. No, you shouldn't panic and start smashing your RFID-enabled credit cards and passports with a hammer. RFID is one of the many ways technology makes life more convenient but can lead to new security and privacy problems. Key Considerations For Successfully Safeguarding Your RFID Card. Taking it to the Next Level in RFID Technology: How to Encrypt RFID Data. Alternatives to Traditional RFID Cards. Wrapping Up and My Experience With RFID Cards and Common Applications of . Here are some key measures to secure RFID systems: Strong encryption algorithms: Implementing strong encryption protocols ensures that the data transmitted between RFID tags and readers is secure and cannot be easily intercepted or decoded by unauthorized parties. Encryption protects against eavesdropping and data tampering.
Use encrypted communication protocol: In the communication between the RFID reader and the card, use a secure communication protocol (such as TLS/SSL) to encrypt the data transmission channel. RFID credit cards are considered safe to use, and credit card fraud using RFID readers is rare and difficult to do. Radio-frequency identification (RFID) credit cards have a type of.
To address this, various advanced encryption technologies have been applied to RFID chips to prevent data breaches and unauthorized access. This article will explore these encryption technologies in detail and introduce several well-known . In short, RFID technology has existed for many decades, but even modern cards can pose a huge vulnerability in your RFID-based security environment if not implemented well. The main risks are that attackers can gain access to your premise through cloning, replaying, relaying and brute-force attacks.
This publication seeks to assist organizations in understanding the risks of RFID technology and security measures to mitigate those risks. It provides practical, real-world advice on how to initiate, design, implement and operate RFID systems in a manner that mitigates security and privacy risks.
rfid encryption
how to use rfid cards
Scanner Radio. Listen to Auburn and Lewiston Fire and EMS. Get the app to listen .Men's Basketball Gameday; Women's Basketball Gameday . live streaming audio of Auburn Sports Network radio broadcasts of Tiger games and coach's shows. . Each .
are rfid cards encrypted|basics of rfid cards