user authentication smart card Smart card authentication requires two things: the smart card itself and a pin entered by the user. With smart cards there are two different ways to authenticate yourself into a system, there is either contact or contactless smart card readers. 50 Authentic Brainstorm ID Inkjet PVC Cards with NTAG215 NFC Chip (13.56MHz, 144 bytes) - The Absolute Best Available, Guaranteed ; .
0 · smart card multi factor authentication
1 · smart card identity
2 · smart card based identification system
3 · smart card authentication step by
4 · smart card authentication protocol
5 · enable smart card log on
6 · enable smart card authentication
7 · authenticate using your smart card
Amiibo cards are flat, credit card-sized devices embedded with an NFC chip, just like amiibo figures. By scanning the card on a compatible Nintendo console, players can access various in-game items, characters, and features, .NFC, or near-field communication, is a short-range wireless technology that allows your phone to act as a transit pass or credit card, quickly transfer data, or instantly pair with Bluetooth .
smart card multi factor authentication
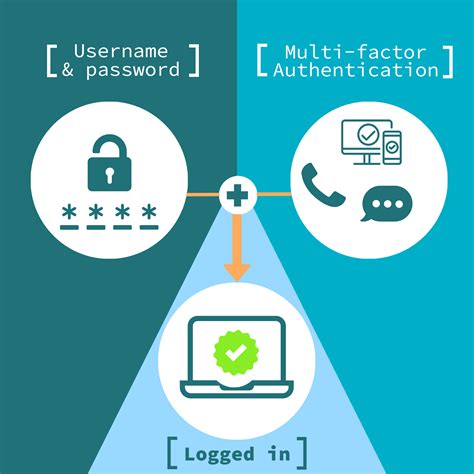
How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system. Typically, a user who signs in to a computer by using a local account or a domain account must enter a user name and password. These credentials are used to verify the user's identity. For smart card sign-in, a user's credentials are .
antenna used in rfid tag
Microsoft Entra users can authenticate using X.509 certificates on their smart cards directly against Microsoft Entra ID at Windows sign-in. There's no special configuration needed on the Windows client to accept the smart card authentication.Smart card authentication requires two things: the smart card itself and a pin entered by the user. With smart cards there are two different ways to authenticate yourself into a system, there is either contact or contactless smart card readers. And while the ISO 7816 form-factor is steadily losing ground (evident by the lack of integrated readers in modern laptops), smart card authentication is experiencing a second coming, a revival brought on by recent mobile and cloud support in Microsoft Azure.
Learn how 1Kosmos enhances smart card authentication with BlockID, offering biometric-based security, identity proofing, privacy by design, distributed ledger technology, interoperability, and industry certifications.Certificate-based authentication is an encrypted method that enables devices and people to identify themselves to other devices and systems. Two common examples are a smart card or when an employee’s device sends a digital certificate to a network or server.
Smart Card Authentication is a means of verifying users into enterprise resources such as workstations and applications using a physical card in tandem with a smart card reader and software on the workstation. Give smart cards to approved users and help them turn on the cards, choose a secret code, and use the cards properly. Provide classes and help for users to learn about smart card logins and get answers to questions or worries. Smart card authentication is a method that employs the embedded chip in the card to verify the identity of the user certificates. The chip can generate or store authentication data through cryptographic algorithms that a reader can verify.
How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system. Typically, a user who signs in to a computer by using a local account or a domain account must enter a user name and password. These credentials are used to verify the user's identity. For smart card sign-in, a user's credentials are . Microsoft Entra users can authenticate using X.509 certificates on their smart cards directly against Microsoft Entra ID at Windows sign-in. There's no special configuration needed on the Windows client to accept the smart card authentication.Smart card authentication requires two things: the smart card itself and a pin entered by the user. With smart cards there are two different ways to authenticate yourself into a system, there is either contact or contactless smart card readers.
And while the ISO 7816 form-factor is steadily losing ground (evident by the lack of integrated readers in modern laptops), smart card authentication is experiencing a second coming, a revival brought on by recent mobile and cloud support in Microsoft Azure. Learn how 1Kosmos enhances smart card authentication with BlockID, offering biometric-based security, identity proofing, privacy by design, distributed ledger technology, interoperability, and industry certifications.Certificate-based authentication is an encrypted method that enables devices and people to identify themselves to other devices and systems. Two common examples are a smart card or when an employee’s device sends a digital certificate to a network or server.Smart Card Authentication is a means of verifying users into enterprise resources such as workstations and applications using a physical card in tandem with a smart card reader and software on the workstation.
Give smart cards to approved users and help them turn on the cards, choose a secret code, and use the cards properly. Provide classes and help for users to learn about smart card logins and get answers to questions or worries.
smart card identity
smart card based identification system
applicator rfid tags wand
smart card authentication step by

The Minnesota Vikings easily beat the Dallas Cowboys, 27 to 10, in the 1999 NFC Wild Card game on January 9, 2000.
user authentication smart card|smart card authentication step by