rfid chip that bur s If a tag has been applied properly and read successfully, there is very little that would cause it to stop working. There are a few issues that companies have run into, however. One thing that could damage a tag is high heat, which can melt the solder connecting the antenna to the chip. Released in June 2018, the NFC Android Smartphone LG G7 ThinQ can scan and use various NFC tags and products thanks to the integrated NFC function. To unlock the LG G7 ThinQ a .LG K20 V specifications; Physical dimensions, weight, and colors . By featuring NFC .
0 · rfid microchip implant
1 · rfid chip breakdown
2 · how to kill rfid tag implant
3 · how to kill a rfid tag
4 · how to kill a rfid implant
5 · how to get rfid implanted
6 · first rfid implant
7 · can rfid tag break down
Phone. Summary. Reading NFC tags via smartphones for scanning assets and inventory is a good option if the volume is low and isn’t required regularly. Pros. Flexible - Can be used as .
If a tag has been applied properly and read successfully, there is very little that would cause it to stop working. There are a few issues that companies have run into, however. One thing that could damage a tag is high heat, which can melt the solder connecting the antenna to the chip.Wannabe-cyborgs with little RFID chips under their skin are living with us: tens of thousands of people implanted the tiny devices already under their skin to have simpler access to buildings or (other people’s) phones. Dr. Bertalan Mesko, .To kill a tag, you need to overload it with energy and blow its circuits. These circuits are tiny, so .If a tag has been applied properly and read successfully, there is very little that would cause it to stop working. There are a few issues that companies have run into, however. One thing that could damage a tag is high heat, which can melt the solder connecting the antenna to the chip.
Wannabe-cyborgs with little RFID chips under their skin are living with us: tens of thousands of people implanted the tiny devices already under their skin to have simpler access to buildings or (other people’s) phones. Dr. Bertalan Mesko, PhD. 9 min | 18 June 2024. Key Takeaways.To kill a tag, you need to overload it with energy and blow its circuits. These circuits are tiny, so even static electricity from your finger can blow them, as long as you are able to touch the chip directly. The problem with an implant is that you can’t touch it, so you can’t get the electricity to the transponder.
When it comes to Tesla cars and SUVs, the "key" isn't a jagged piece of metal but rather a key card that contains a radio frequency identification (RFID) chip that can be wirelessly read by the. Discover the signs and symptoms of having a RFID chip implanted in your body and find out how to determine if you are being tracked or monitored.

how to change photo in smart card tamilnadu
Researchers at North Carolina State University have created what they say is the smallest-ever second-generation radio-frequency identification (RFID) chip — paving the way to lower-cost RFID tags and tags embeddable in new devices, including silicon chips. Radiofrequency identification (RFID) chip implantation is increasing in the context of the growing body hacking movement. RFID chips may be used for personal identification and for contactless payments and other secure transactions.Passive RFID tags harness energy from an RFID reader’s emitted Radio-frequency (RF) signal. When the reader sends a signal, it creates an electromagnetic field that energizes the tag. The tag captures this energy and powers its internal chip, enabling it to transmit data back to the reader. RFID chips are a convenient way to store and access data, but they can also be vulnerable to malicious attacks. Hackers can use RFID scanners to steal money from your phone’s tap-to-pay app, or clone the chip and gain access to a system or data.
An RFID chip is typically a simple piece of hardware with a unique identifier and a small amount of read/write storage. Currently, this storage is insufficient for significant medical information, so the chip usually stores only a patient identifier, which links .If a tag has been applied properly and read successfully, there is very little that would cause it to stop working. There are a few issues that companies have run into, however. One thing that could damage a tag is high heat, which can melt the solder connecting the antenna to the chip.Wannabe-cyborgs with little RFID chips under their skin are living with us: tens of thousands of people implanted the tiny devices already under their skin to have simpler access to buildings or (other people’s) phones. Dr. Bertalan Mesko, PhD. 9 min | 18 June 2024. Key Takeaways.To kill a tag, you need to overload it with energy and blow its circuits. These circuits are tiny, so even static electricity from your finger can blow them, as long as you are able to touch the chip directly. The problem with an implant is that you can’t touch it, so you can’t get the electricity to the transponder.
When it comes to Tesla cars and SUVs, the "key" isn't a jagged piece of metal but rather a key card that contains a radio frequency identification (RFID) chip that can be wirelessly read by the.
Discover the signs and symptoms of having a RFID chip implanted in your body and find out how to determine if you are being tracked or monitored.
Researchers at North Carolina State University have created what they say is the smallest-ever second-generation radio-frequency identification (RFID) chip — paving the way to lower-cost RFID tags and tags embeddable in new devices, including silicon chips. Radiofrequency identification (RFID) chip implantation is increasing in the context of the growing body hacking movement. RFID chips may be used for personal identification and for contactless payments and other secure transactions.Passive RFID tags harness energy from an RFID reader’s emitted Radio-frequency (RF) signal. When the reader sends a signal, it creates an electromagnetic field that energizes the tag. The tag captures this energy and powers its internal chip, enabling it to transmit data back to the reader. RFID chips are a convenient way to store and access data, but they can also be vulnerable to malicious attacks. Hackers can use RFID scanners to steal money from your phone’s tap-to-pay app, or clone the chip and gain access to a system or data.
rfid microchip implant
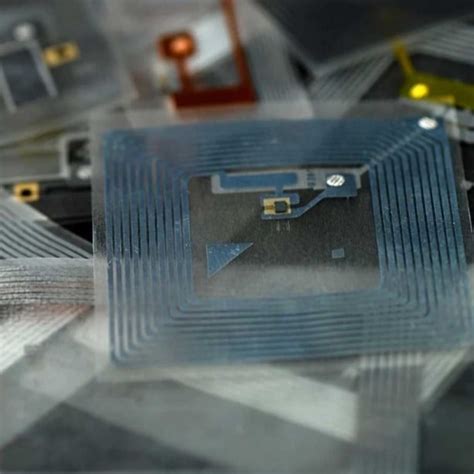
But there are some other factors, like coupling factor between the reader .You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. Reload to refresh your session. You switched accounts on another tab or window.
rfid chip that bur s|how to kill rfid tag implant