rfid badge hack statistics current RFID protocols are designed to optimize performance, with lesser attention paid to resilience and security. Consequently, most RFID systems are inherently insecure. In this . You can try NFC Tools or the MiFare Classic Tool to emulate cards from your phone, but in my experience it's too limited. NFC tools can emulate tags but I've tried it with hotel keys and it .
0 · what is rfid security
1 · rfid vulnerabilities
2 · rfid security problems
3 · rfid security and prevention
4 · rfid cyber security vulnerabilities
5 · rfid card attacks
6 · rfid attacks list
7 · low cost rfid security
Step 12: Revision II: NFC Edition. My PCB layout business cards served me well and were a good conversation starter at conferences and events. As I came across more and more business card designs, especially those integrated .
Learn how to prevent RFID hacking with our comprehensive guide. Increase your business safety and convenience while eliminating RFID attacks. Click here!With the increasing use of RFID technology, it is crucial to recognize the importance of cybersecurity. As objects become more interconnected, they also become vulnerable to cyber .
current RFID protocols are designed to optimize performance, with lesser attention paid to resilience and security. Consequently, most RFID systems are inherently insecure. In this .
windows smart card service
June 9, 2022. Summary: Products such as “RFID wallets” claim to prevent frauds and scams like RFID skimming, in which thieves steal information off your chip-embedded credit card. Be wary of these claims; there are better forms of .By understanding the basics of RFID technology, comprehending the threats posed by RFID hacking, and implementing robust protection strategies, organizations can safeguard their . This paper develops a structural methodology for risks that RFID networks face by developing a classification of RFID attacks, presenting their important features, and discussing . RFID hackers have demonstrated how easy it is to get hold of information within RFID chips. As some chips are rewritable, hackers can even delete or replace RFID .
RFID is radio-based tech that can be exploited by hackers. Learn how to prevent RFID Hacking with seven security tips.
what is rfid security
Besides being vulnerable to common attacks such as eavesdropping, man-in-the-middle, and denial of service, RFID technology is, in particular, susceptible to spoofing and power attacks . Learn how to prevent RFID hacking with our comprehensive guide. Increase your business safety and convenience while eliminating RFID attacks. Click here!

RFID cards many times contain a facility code or other specific identifiers that cannot be quickly guessed. If an attacker captures that data from a known-valid card, the final identifier of another employee’s RFID credentials can .With the increasing use of RFID technology, it is crucial to recognize the importance of cybersecurity. As objects become more interconnected, they also become vulnerable to cyber attacks. Imagine if a hacker could gain unauthorized access to .
current RFID protocols are designed to optimize performance, with lesser attention paid to resilience and security. Consequently, most RFID systems are inherently insecure. In this paper, we discuss four common types of RFID tag attacks .
June 9, 2022. Summary: Products such as “RFID wallets” claim to prevent frauds and scams like RFID skimming, in which thieves steal information off your chip-embedded credit card. Be wary of these claims; there are better forms of identity theft .By understanding the basics of RFID technology, comprehending the threats posed by RFID hacking, and implementing robust protection strategies, organizations can safeguard their RFID systems and protect their valuable assets and sensitive information from .
This paper develops a structural methodology for risks that RFID networks face by developing a classification of RFID attacks, presenting their important features, and discussing possible countermeasures.
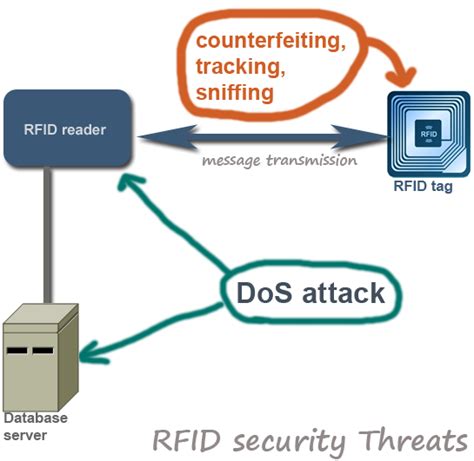
RFID hackers have demonstrated how easy it is to get hold of information within RFID chips. As some chips are rewritable, hackers can even delete or replace RFID information with their own data. It's not too tricky for a hacker build his or . RFID is radio-based tech that can be exploited by hackers. Learn how to prevent RFID Hacking with seven security tips.Besides being vulnerable to common attacks such as eavesdropping, man-in-the-middle, and denial of service, RFID technology is, in particular, susceptible to spoofing and power attacks (Figure 2). This section illustrates different kinds of attacks and provides countermeasures against these attacks. Fig. 2.
Learn how to prevent RFID hacking with our comprehensive guide. Increase your business safety and convenience while eliminating RFID attacks. Click here! RFID cards many times contain a facility code or other specific identifiers that cannot be quickly guessed. If an attacker captures that data from a known-valid card, the final identifier of another employee’s RFID credentials can .
where to get smart card
With the increasing use of RFID technology, it is crucial to recognize the importance of cybersecurity. As objects become more interconnected, they also become vulnerable to cyber attacks. Imagine if a hacker could gain unauthorized access to .current RFID protocols are designed to optimize performance, with lesser attention paid to resilience and security. Consequently, most RFID systems are inherently insecure. In this paper, we discuss four common types of RFID tag attacks .June 9, 2022. Summary: Products such as “RFID wallets” claim to prevent frauds and scams like RFID skimming, in which thieves steal information off your chip-embedded credit card. Be wary of these claims; there are better forms of identity theft .By understanding the basics of RFID technology, comprehending the threats posed by RFID hacking, and implementing robust protection strategies, organizations can safeguard their RFID systems and protect their valuable assets and sensitive information from .

This paper develops a structural methodology for risks that RFID networks face by developing a classification of RFID attacks, presenting their important features, and discussing possible countermeasures. RFID hackers have demonstrated how easy it is to get hold of information within RFID chips. As some chips are rewritable, hackers can even delete or replace RFID information with their own data. It's not too tricky for a hacker build his or .
rfid vulnerabilities
rfid security problems
RFID is radio-based tech that can be exploited by hackers. Learn how to prevent RFID Hacking with seven security tips.
write certificate to smart card
rfid security and prevention
This means you can copy the tag's UID with an app like MIFARE Classic Tool. When .
rfid badge hack statistics|rfid attacks list