biometric identification alternatives to rfid chips Nanotechnology: Microscopic identification methods using nanotechnology could become more prevalent in the future. For example, tiny RFID (Radio-Frequency Identification) chips or . Have a look at the number 14 in the footnotes at the bottom of this link: iOS 14 - .
0 · rfid key card vs biometric
1 · keyless vs local biometrics
2 · keyless biometrics
3 · device native vs local biometric
4 · device native biometrics
5 · can biometrics be used
6 · biometric authentication systems
7 · are biometric authentication systems safe
The Steps: 1: Plug in you NFC reader/writer into the port on your computer. There should be a light on it that lights up red. When putting an NFC item on the platform the unit should beep and the light should turn green, removing the .In my project, we used ACR122 smart card reader that will be connect to a pc not android device.This reader is used to read any nfc tag. An nfc enabled android device will act as a nfc tag in card emulation mode. Now next part of question "The inbuilt NFC libraries support to .
Discover the key differences between RFID key cards and biometric access control systems. Learn which technology offers better security, convenience, and cost-effectiveness for your specific needs. Learn about device-native and server-side biometrics including their advantages, disadvantages, and potential alternatives to traditional methods.
Nanotechnology: Microscopic identification methods using nanotechnology could become more prevalent in the future. For example, tiny RFID (Radio-Frequency Identification) chips or .Discover the key differences between RFID key cards and biometric access control systems. Learn which technology offers better security, convenience, and cost-effectiveness for your specific needs. Learn about device-native and server-side biometrics including their advantages, disadvantages, and potential alternatives to traditional methods.
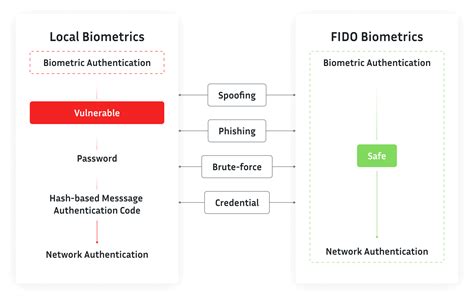
Nanotechnology: Microscopic identification methods using nanotechnology could become more prevalent in the future. For example, tiny RFID (Radio-Frequency Identification) chips or nanoscale identifiers could be embedded in documents or even directly in the human body for secure identification. The combination of FIDO2 and FIDO Biometric Component certification gives Keyless’ customers assurance of the effectiveness of the company’s approach to performing biometric authentication on a distributed network rather than locally, Co-founder and CTO Paolo Gasti and VP Product Gal Steinberg tell Biometric Update in an interview. The .
The five most common types of biometric identifiers are: fingerprints, facial, voice, iris, and palm or finger vein patterns. As an example, banks need your biometric data in order to provide their various services remotely.
When combined with biometric verification, NFC-based identification can be used to enhance user experience while ensuring a high level of trust at a lower cost and in real-time. All the users need is NFC-enabled ID Document and a smartphone with NFC Capabilities and biometric sensors. 1. Fingerprint Recognition. 2. Facial Recognition. 3. Eye Recognition. 4. Voice Recognition. 5. Hand Geometry. 6. Signature Recognition. Key Features of Biometric Authentication Tools. 3 Ways to Integrate Biometrics with Your Applications. Authn: Driving the Biometric Revolution. Face ID for Apple Users. Android Biometrics. Biometric identification technologies—such as facial recognition and fingerprinting—can affect underserved communities, including low-income and minority communities. We interviewed academics, advocacy groups, and technology experts to .
Biometric technology offers high accuracy and offers better security than RFID systems. Biometric readers can scan and authenticate a person's actual physical characteristics and validate their identity.
Identification using RFID also works better and facilitates the identification process in many ways like high storage capacity, automatic scanning, etc. But there still remains a chance to mix-up the patients if the staffs fail to tag the exact RFID to .Discover the key differences between RFID key cards and biometric access control systems. Learn which technology offers better security, convenience, and cost-effectiveness for your specific needs. Learn about device-native and server-side biometrics including their advantages, disadvantages, and potential alternatives to traditional methods.Nanotechnology: Microscopic identification methods using nanotechnology could become more prevalent in the future. For example, tiny RFID (Radio-Frequency Identification) chips or nanoscale identifiers could be embedded in documents or even directly in the human body for secure identification.
The combination of FIDO2 and FIDO Biometric Component certification gives Keyless’ customers assurance of the effectiveness of the company’s approach to performing biometric authentication on a distributed network rather than locally, Co-founder and CTO Paolo Gasti and VP Product Gal Steinberg tell Biometric Update in an interview. The .
The five most common types of biometric identifiers are: fingerprints, facial, voice, iris, and palm or finger vein patterns. As an example, banks need your biometric data in order to provide their various services remotely. When combined with biometric verification, NFC-based identification can be used to enhance user experience while ensuring a high level of trust at a lower cost and in real-time. All the users need is NFC-enabled ID Document and a smartphone with NFC Capabilities and biometric sensors. 1. Fingerprint Recognition. 2. Facial Recognition. 3. Eye Recognition. 4. Voice Recognition. 5. Hand Geometry. 6. Signature Recognition. Key Features of Biometric Authentication Tools. 3 Ways to Integrate Biometrics with Your Applications. Authn: Driving the Biometric Revolution. Face ID for Apple Users. Android Biometrics.
Biometric identification technologies—such as facial recognition and fingerprinting—can affect underserved communities, including low-income and minority communities. We interviewed academics, advocacy groups, and technology experts to .
Biometric technology offers high accuracy and offers better security than RFID systems. Biometric readers can scan and authenticate a person's actual physical characteristics and validate their identity.

rfid key card vs biometric
smart card metro
smart card how to
Probably not. The NDEF record can include both a password and a Lock. Even if there is no password, a NFC tag that is locked is basically locked forever. Passwords only can be hacked (requires programming skills) but no way .
biometric identification alternatives to rfid chips|rfid key card vs biometric