copy rfid tags Ever had a receptionist have a go at you for losing your fob? Ever had them ramble on about how not to place it close to your phone - just in case, as if lik.
2017 NFL playoffs schedule, Super Bowl LII coverage. play. Young: Foles outdueled Brady (2:33) . NFC wild-card round (6) Atlanta Falcons 26, (3) Los Angeles Rams 13.
0 · what rfid tag will do
1 · rfid tags for home use
2 · rfid radio frequency identification tags
3 · rfid is involved when using
4 · rfid for dummies
5 · rfid cards for beginners
6 · radio frequency identification tags are
7 · example of rfid tags
Jan 25, 2014. #1. Ok maybe not oyster but the equivilent here. It uses NFC technology, using a raspberry pi and an NFC card reader, I purchased an anonymous card and put a tenner on it. .
In this article, we will guide you through the process of copying an RFID card. This step-by-step guide will help you understand the technology behind RFID cards, the tools . Step-by-Step Tutorial: How to Copy or Clone Access Cards and Key Fobs. Access credentials are prone to hacking. This post explains how easy it is to copy access cards with Flipper Zero, off-the-shelf hardware, and an app. 10 min reading time. In this article, we will guide you through the process of copying an RFID card. This step-by-step guide will help you understand the technology behind RFID cards, the tools required for cloning, and the necessary steps to successfully create a duplicate card.
Learn how to easily copy your RFID card to your iPhone using simple steps and start accessing your favorite places with just a tap!
With the advent of technology, it is now possible to copy an NFC card to your phone. This can be done with the help of Rango NFC, provided your device is rooted. To clone a card, hold the card you want to clone against your phone and let the app detect the UID and length.Ever had a receptionist have a go at you for losing your fob? Ever had them ramble on about how not to place it close to your phone - just in case, as if lik. Enhance your access control system, increase convenience, and enjoy the benefits of having cloned RFID fobs at your fingertips. Learn the step-by-step process of duplicating an RFID fob, from cloning to programming, and ensure seamless access control to your belongings.
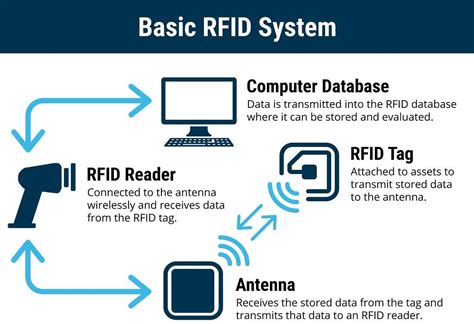
Copying Data: You can copy the extracted data using a cloning device or software. This process involves programming the copied fob with the same unique identification code as the original tag, effectively creating an identical copy.Each RFID chip has a unique serial number that cannot be changed, which identifies the chip as unique. A serial number is then written to the tag’s memory. You could read the TID and serial number and make sure there was a correct match, in order to ensure the tag was not cloned.RFID copiers work by copying the unique information on unencrypted key fobs, key tags, and key cards to a different device. All RFID-compatible access credentials feature an IC (integrated circuit) and a small antenna that picks up radio frequency waves.Copy your RFID to any style! We offer different types of key fobs and cards. Fits on your keychain or in your pocket, wallet, or lanyard; Styles sent via mail are shipped inside an RFID-blocking sleeve
Step-by-Step Tutorial: How to Copy or Clone Access Cards and Key Fobs. Access credentials are prone to hacking. This post explains how easy it is to copy access cards with Flipper Zero, off-the-shelf hardware, and an app. 10 min reading time.
what rfid tag will do

In this article, we will guide you through the process of copying an RFID card. This step-by-step guide will help you understand the technology behind RFID cards, the tools required for cloning, and the necessary steps to successfully create a duplicate card. Learn how to easily copy your RFID card to your iPhone using simple steps and start accessing your favorite places with just a tap!
contactless card how it works
With the advent of technology, it is now possible to copy an NFC card to your phone. This can be done with the help of Rango NFC, provided your device is rooted. To clone a card, hold the card you want to clone against your phone and let the app detect the UID and length.Ever had a receptionist have a go at you for losing your fob? Ever had them ramble on about how not to place it close to your phone - just in case, as if lik. Enhance your access control system, increase convenience, and enjoy the benefits of having cloned RFID fobs at your fingertips. Learn the step-by-step process of duplicating an RFID fob, from cloning to programming, and ensure seamless access control to your belongings.
Copying Data: You can copy the extracted data using a cloning device or software. This process involves programming the copied fob with the same unique identification code as the original tag, effectively creating an identical copy.Each RFID chip has a unique serial number that cannot be changed, which identifies the chip as unique. A serial number is then written to the tag’s memory. You could read the TID and serial number and make sure there was a correct match, in order to ensure the tag was not cloned.RFID copiers work by copying the unique information on unencrypted key fobs, key tags, and key cards to a different device. All RFID-compatible access credentials feature an IC (integrated circuit) and a small antenna that picks up radio frequency waves.
rfid tags for home use

rfid radio frequency identification tags

oyster card vs contactless card
is contactless card safe
Shop the T Mobile Sim Card 4g 5g with features, pricing and reviews. Pair it with .
copy rfid tags|rfid for dummies